
Back in the days when the internet was young, communication was a simple matter. Users needed a communications protocol that was fast and scalable. So, that’s what developers delivered: the user datagram protocol (UDP) for the internet’s domain naming system (DNS).

Let’s set the nostalgia aside for a moment. You probably recognize the problem lurking in this cyber-folk tale. DNS communications was a pillar of internet communications in the 1990s. It’s still an essential part of every Internet transaction. However, it’s increasingly difficult for DNS servers to withstand distributed denial of service (DDoS)attacks today.
These days, network performance is measured in terms of security as well as communications speed and scalability. The performance that served users well enough in the early days of the internet needs modernizing today.
What’s new with DNS attacks
In the past, large attacks on DNS servers typically used familiar methods that multiply the effect of DDoS attacks and redirect it back to the servers. The growth of the IoT has made it easy for attackers to capture the computing power of hundreds of thousands of insecure devices. When hackers use these devices (bots) in botnets, they can engage in sophisticated application-layer attacks, specifically in DNS servers.
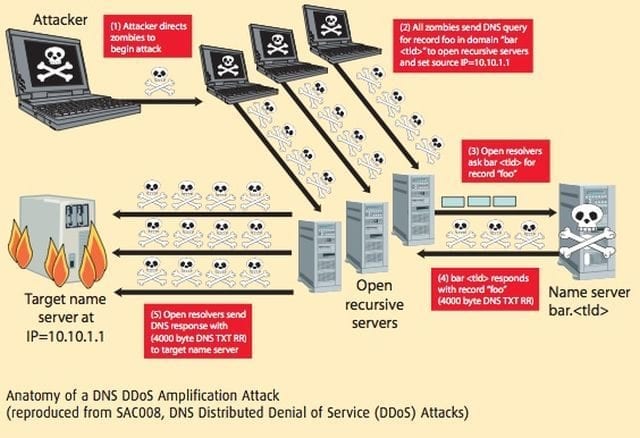
Gartner predicts that, by 2024, the global internet will connect more than 20 billion IoT devices. This presents a serious problem. Internet infrastructure capacity grows more slowly than the number of IoT devices. The likely results: not only more attacks but attacks that are more frequent, powerful, and sophisticated.
Since the Mirai botnet attack in October 2016, hackers use reflection and amplification methods less often. Now, there’s a surge of new and improved IoT botnets running advanced DDoS attacks on DNS server apps.
DNS attacks, old and new
The variety and complexity of attacks on DNS servers provide a certain grim fascination. There are quite a few types of attacks, and they all involve a complex back-and-forth between clients and DNS servers. IT security pros recognize DDoS, DNS hijacking, spoofing, and other familiar types of DNS attacks. However, there’s a new breed of next-generation DNS attacks that are making their mark on networks everywhere.
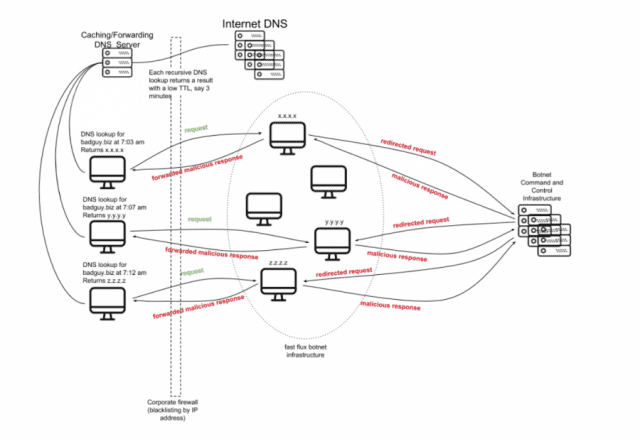
Fast-flux DNS. This technique assigns several IP addresses to the same domain and changes them back and forth, in rapid-fire succession. Attackers swap the DNS records to redirect DNS requests and avoid detection. Often, fast-flux attacks hide attackers’ malware and phishing campaigns.
DNS water-torture DDoS attacks. In a typical DNS water torture attack, hackers use a botnet to create hundreds of thousands of DNS requests. The requests, which are made for phony subdomains, use up memory and processing resources on the main DNS server. From the legitimate user’s point of view, resources run slowly or stop altogether. Before you know it, a new type of DDoS exploit is born.
Expired domain takeovers and redirection. When companies forget the names and status of their domains, pain often follows. Of course, hackers are all too eager to take advantage of the memory lapse. In this exploit, hackers register expired domain information to divert customer traffic to some very strange destinations—gambling, click-fraud, or malware-for-hire operations.
But what makes DNS servers so difficult to secure? The answer goes back to the origins of the UDP protocol and the internet.
Why hackers love to attack DNS targets
There are two simple reasons why DNS servers are such attractive attack targets. First, the UDP protocol underlies DNS systems, which are an essential part of the internet. Second, DNS servers are absurdly easy to hack.
But, why?
Hardly anyone pays attention to DNS infrastructure. In the rush of evolving cyber threats and technology, many organizations lose track of the DNS part of their IT operations. DNS-related network behavior goes unmonitored, and DNS software doesn’t get modernized. More than 86 percent of companies that leave DNS servers unmonitored fail to modernize their DNS infrastructure. That means, DNS-based cyber attacks continue to evolve, but dated DNS server software will probably fail to defend networks against sophisticated attacks.
DNS infrastructure has serious shortcomings. DNS infrastructure cannot evaluate whether IP addresses in queries are legitimate or malicious. Attackers exploit this unprotected infrastructure and design attacks that use fake queries and responses. Even when vendors develop and deploy advanced security solutions, these attacks make DNS infrastructure vulnerable to a growing variety of attacks.
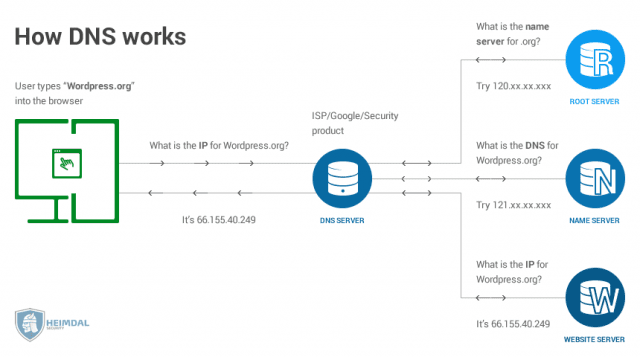
Easy access to DNS infrastructure is also a problem. Most firewalls don’t inspect the DNS server port, where queries are made. This weakness is an “open, sesame!” that gives anyone, including hackers, access to DNS services. And finally, DNS services provide cover for hackers to hide in. To maintain high-speed performance, DNS infrastructure was designed with a stateless protocol. That design approach made it very attractive to attackers, who can easily hide their identity and launch attacks on DNS servers.
Revitalizing legacy DNS capabilities
Like it or not, weaknesses in DNS infrastructure are part of Internet technology. And DNS-related attacks continue to become more sophisticated and powerful. Protecting aging DNS services requires advanced protection. In other words, you’ll need heavy firepower to fill the security gaps of DNS infrastructure.
Third-party attack mitigation services are probably the most effective way to ensure that your DNS infrastructure can stand up to the hurricane blast of modern DDoS attacks. The more advanced name service security:
- Provides always-on service.
- Enables DDoS mitigation in seconds.
- Protects applications and network infrastructure against all DoS exploits.
- Prevents illegal DNS queries from reaching your servers.
- Protects DNS servers from direct-to-IP network layer attacks.
- Makes it easy to monitor and understand your network’s status and behavior.
- Enables you to manage your DNS zone files outside of Incapsula network.
Adding cloud-based attack mitigation services also provides highly scalable services that can accommodate networks of any size and location.
Secure, reliable DNS services are real and available right here, right now. You can modernize aging DNS security capabilities on any network by engaging a DDoS mitigation service provider. So, instead of getting nervous when you hear the term, “DNS security,” why not modernize?





